
Upgrade to the crypto wallet with no seed phrase vulnerability, powered and secured by MPC (Multi-Party Computation): Technology used by institutions to custody billions of dollars of crypto. Zengo maintains the world’s largest open-source MPC library and holds multiple patents in consumer wallet security innovation.
Our security model speaks for itself: 0 Zengo wallets have been hacked or stolen since founding in 2018. Learn more below.

Zengo is the first crypto wallet to leverage MPC’s advanced security features for a consumer-based wallet, offering a self-custodial wallet with no seed phrase vulnerability. This is an order of magnitude more secure than seed phrase-based wallets: Even hardware wallets.
MPC (Multi-Party Computation) cryptography has been used at the institutional level for years to custody billions of dollars by companies like Fireblocks and Coinbase.
Zengo is the first crypto wallet to leverage MPC’s advanced security features for a consumer wallet, offering a self-custodial wallet with no seed phrase vulnerability. This is an order of magnitude more secure than seed phrase wallets: Even hardware wallets.
Traditional wallets rely on a seed phrase to interface with the blockchain. This singular vulnerability has led to seed phrase phishing, theft, and wallet misplacement. Over $100 billion dollars of Bitcoin has been lost or stolen in the last decade due to seed phrase mismanagement.
MPC wallets offer an order of magnitude more security than seed phrase based wallets: Leveraging MPC architecture allows Zengo users to self-custody without seed phrases.
Instead of the traditional seed phrase, Zengo is powered by two independently-created “secret shares.” One share (your Personal Share) is created and stored on your mobile device. The second share (your Remote Share) is created and secured on ZenGo’s servers.
Every time you initialize a transaction from your wallet, the two secret shares securely compute to create a signed transaction which interfaces with the blockchain.
Zengo’s security model removes the single point of failure found in traditional wallets (a vulnerable seed phrase). When you create your Zengo wallet for the first time, two secret shares are initialized: The Personal Share, which is stored on your mobile device, and the Remote Share, which is stored on Zengo’s servers.
Zengo’s 3FA recovery system allows you to recover your wallet if you’re moving your account to a new device using
1) Something you control; 2) Something you are; and 3) Something you store.
3D FaceLock is a biometric liveness scan that ties your Zengo account to you. This mathematical representation of your face is encrypted, scrambled and accessible to no one but you.
Security tip: Add a secondary 3D FaceLock should something happen to the first one.
The Recovery File, securely stored in at least one of your cloud backup locations (iCloud/Google Drive and Dropbox). This file can only be unlocked by you and is useless to a hacker.
Security tip: Backup your Recovery File in more than one location.
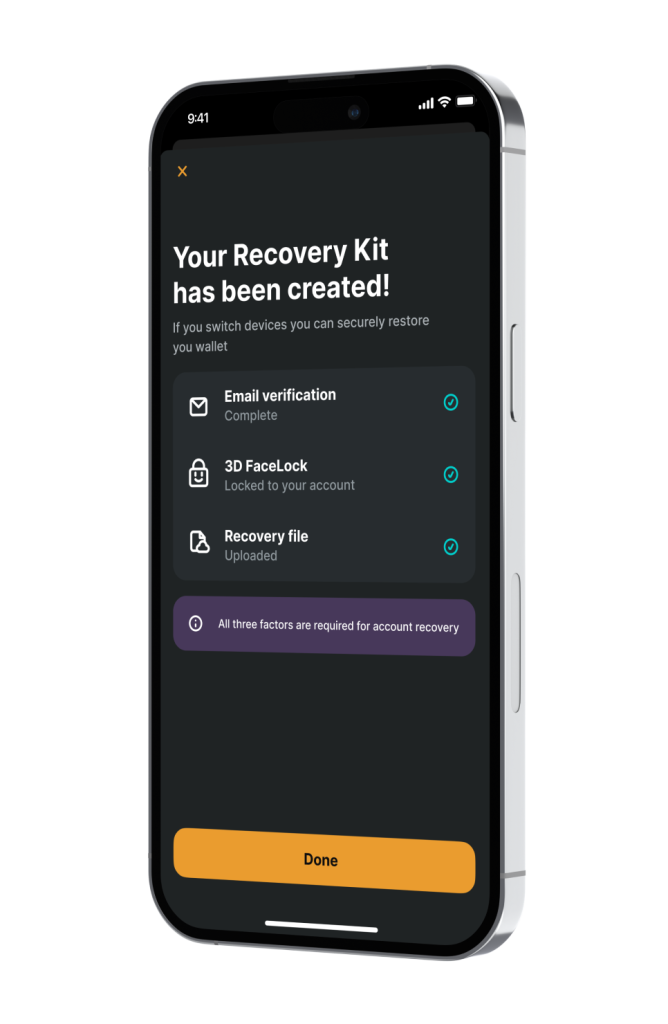
It only takes a few moments to recover your wallet. Simply confirm your email address, authenticate using
3D FaceLock, and the encrypted Personal Share is then decrypted on your device – restoring full access to your account.
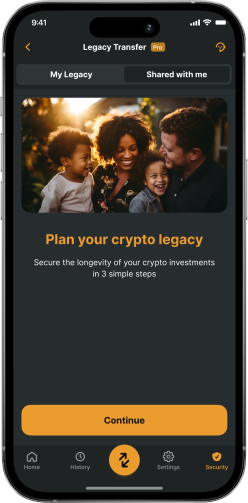
Legacy Transfer is an inheritance-style solution for digital assets inside any Zengo wallet. Legacy Transfer will empower any Zengo user to designate a future recipient for their digital assets in a way that maintains full user control: They can cancel or change their designated recipient at any time, and no private keys or seed phrases are required, rendering the system more secure and less complicated than alternatives. Legacy Transfer is triggered after a pre-determined inactivity period expires.
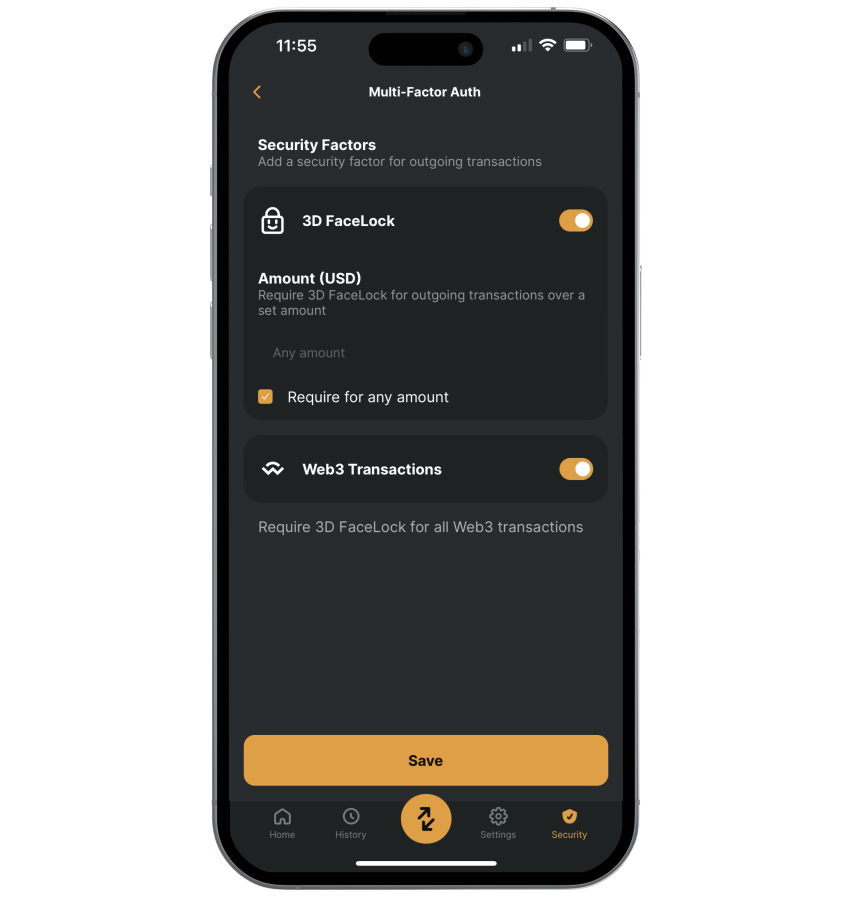
Prevent unauthorized withdrawals with 3D FaceLock biometric verification.
Set a custom amount to trigger the multi-layered approvals process. Even a friend or trusted loved one with access to your phone can’t approve these withdrawals – only you can with Zengo’s 3D FaceLock verification process.
Zengo’s advanced Web3 firewall alerts, informs, and protects you against approving the most sensitive and vulnerable Web3 attacks. Sensitive on-chain transactions are classified into 3 risk levels, based on transaction sensitivity, levels of permission granted to the external systems, and known scams. Just like a stoplight, with 3 levels of safety. You can finally engage with web3 in confidence.
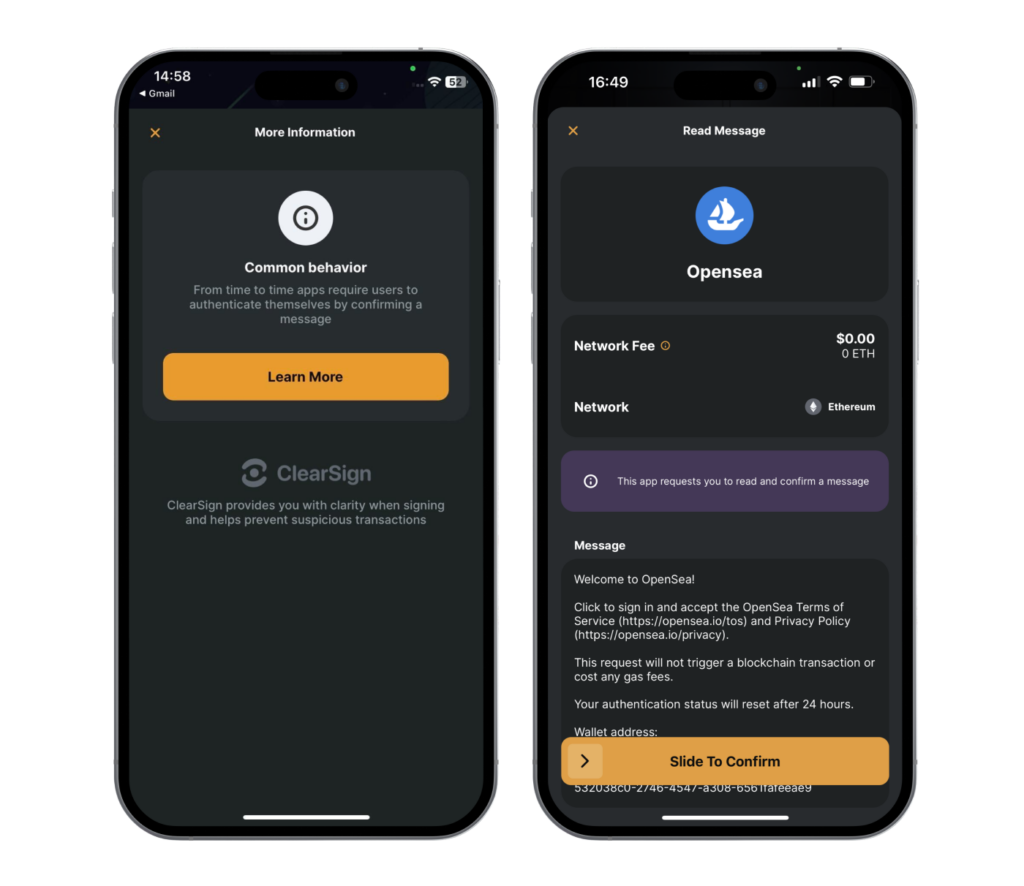
You are interacting with a verified Dapp and/or known smart contract. Look for the green checkmark during the signing process.
Depending on the context, you are interacting with an app that reflects uncommon behavior: Stay alert and confirm that intent is aligned with expected results.
ClearSign has detected highly unusual behavior and immediate attention is required. Most of the most sensitive red transactions require a double-confirmation.

No matter where you on your crypto journey, Zengo’s expert support team is a simple tap away, 24/7, directly inside of the app.
Zengo Pro’s Priority Support takes this a step further with guaranteed response times in 1 hour or less, a dedicated team comprised of our most experienced support staff, and customized updates to fit your needs.
No. Zengo’s 3FA recovery process requires 3 security factors you control, including your email, the Recovery File stored in the cloud of your choice, and your 3D FaceLock.
Should an attacker get access to your email or your cloud recovery file, they would not be able to recover and access your Zengo account because your 3D FaceLock would still be required. Since Zengo was established in 2018, not one account has been hacked or stolen.
As long as your wallet is backed-up you should have no issues accessing your assets.
However, Zengo is a self-custodial wallet, which means you are ultimately responsible for your assets. We try to make this as easy and foolproof as possible, and there are extra steps you can take to ensure redundancy if you ever need to recover your wallet.
You can lose your funds on Zengo if both of these things were to happen: 1) You lose your device and need to recover it and 2) You lose access to one or more of the 3 factors necessary to authenticate your wallet recovery.
To mitigate that, you are encouraged to add a secondary email address, a secondary recovery kit using Google drive or Dropbox, and a secondary 3D FaceLock connected to your account. Learn more here.
No. As long as you have your email, Recovery File and 3D FaceLock, you will always be able to recover your account; You can also recover your account by moving from iPhone to Android by using Google Drive with your Zengo Recovery Kit.
However if someone gets physical access to your phone with Zengo on it and that same person has access to your device passcode, your Zengo account is at risk as well as all other apps on your phone (just as if someone has access to a hardware wallet’s PIN code). Zengo Pro customers with Theft Protection enabled are secure even from this risk – not even a hardware wallet can do this! It is therefore important you choose a strong device security PIN that is very hard to find to protect the access to your device. For added security, Zengo won’t even let you receive assets until your phone’s device lock is activated.
Zengo gives you additional security by allowing you to add a second trusted 3D FaceLock to recover your account. Should your face change meaningfully, you would be able to recover your account with the assistance of that person.
Note that minor changes like natural aging, a scar, or a light beard do not have any impact.
No. We have a guaranteed access solution so this never happens. Learn more here.
No, never.
Zengo is self-custodial and account recovery relies on 3 security factors. Zengo does not have access to your personal share (stored on your personal cloud) or email address, both of which are necessary to access your account.
No. The technology used is resistant to the most sophisticated spoofing attacks. Learn more here.
No. Zengo has been in operation since 2018. Not one account has been hacked or taken over since the company was founded.
Yes. We regularly perform formal and external security audits on our apps made by reputable firms. Our MPC cryptography is open-source, audited and peer-reviewed.
All transactions in your Zengo wallet can only be initialized by you, and Zengo can never spend your funds or access the assets in your wallet.
Zengo’s MPC security system requires that any transaction you make be validated by Zengo’s servers before being broadcasted to the blockchain. This adds an additional layer of security for all Zengo users, and helps guarantee the integrity of your transactions, including hacks, fraud detection, and other types of risks. For example: Your built-in Web3 firewall – ClearSign – does not block transactions with blockchain apps that are marked as risky but only informs you clearly about the risks associated. You can always bypass this safety notification: Ultimately you are responsible for your assets and how you want to use them.
While in theory this secure architecture could be used to prevent certain transactions from being broadcasted, Zengo has never done so – ever since the company was founded.
Zengo has no access to any private information about you besides your email, and this email can be non-nominative should you choose.
Zengo does not provide investment or trading services. Instead, we partner with vetted partners that offer these services. Each partner is clearly disclosed and you are invited to agree to their terms and conditions before using them. Although we spend a considerable amount of time selecting these partners for you, it is important you take the time to read and understand how they operate and their respective security models.
© 2024 Zengo Ltd. All rights reserved.
Enter your phone number to receive a download link.
