Recently we had publicly shared the Curv library as an open source project under the permissive MIT License. In this blog post we would like to share some details and context of this library.

What is Curv Library?
Simply put, Curv is the starting point for all elliptic curve cryptographic protocols. It is a gateway that translate low level implementations of the math beyond various elliptic curves into easy to use and read operations and cryptographic primitives. Here is an example for proof of knowledge of dlog (code):
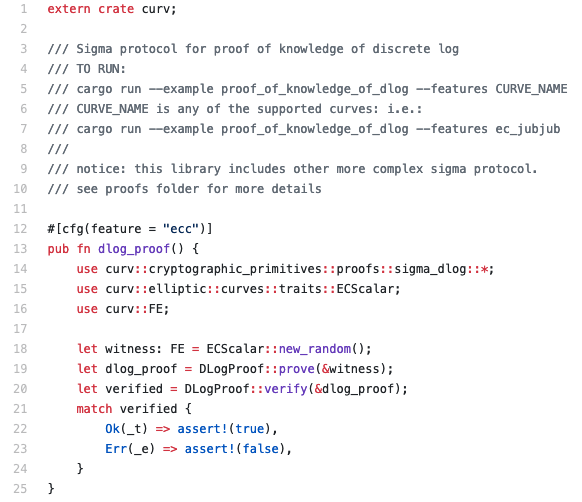
We had built into the library some useful building blocks that you might want to use while implementing your protocol. We welcome new features, so if you write some cool basic building block that is generic enough, please share. Otherwise all basic operations are supported.
Suggested user flow: choose an Elliptic Curve (EC) -> write the interface if the EC is not supported -> use operations and field elements and group elements and basic primitive to build your awesome protocol. At KZen we follow this recipe all the time (See here).
Why Curv Library?
We had started this effort out of necessity. We at KZen are developing a cross chain threshold signature based wallet and therefore we needed a library that would:
Support the required crypto primitives for threshold cryptography: Such as verifiable secret sharing, commitment schemes, zero knowledge proofs, and simple two party protocols such as ECDH and coin flip.
Be written in Rust: for superior security and performance
Provide a unified interface for many types of Elliptic Curves used by all kind of blockchains: naturally Secp256k1 for Bitcoin and Ethereum, but also Ed25519 used by Ripple, Tezos and Cardano, Jubjub used by Zcash and others.
Since we could not found such existing library we decided to develop it on our own and give back to the community by sharing it.
Curv Library Security
The library was audited by Kudelski security on February 2019. The report can be found here. We are happy to share that no critical issue were found and all other secondary issues found were fixed.

The code was reviewed independently by few other cryptographers. Special thanks goes to our advisor, Prof. Claudio Orlandi of Aarhus University.
In general, the security of the library is strongly dependent on the security of the low level libraries used. We chose only libraries that are used as part of other big projects and went through heavy audit/review.
The library is not immune to side channel attacks but considerable effort was given to try and catch as many such attacks as possible (see audit report).
What’s next?
Well that’s up to you! Please go ahead, use the library in your projects and contribute in any way: add more Elliptic Curves, audit the code or open issues and offer features via pull requests. We’d love to get your contributions.
